Understanding Attribute Based Access Control (ABAC)
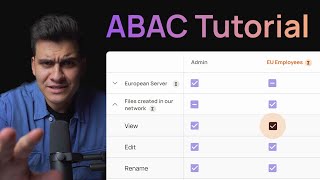
There are a few widely known authorization methods used today. The popular one is Rolebased access control (RBAC). However, RBAC does have its limitations. Another method is attributebased access control (ABAC), where you can use specific attributes, the specific object you want to allow access to, and the specific operations (create, run, delete, view, etc) allowed. Using attributes with welldefined policies, organizations can grant specific access to networks, applications, and much more.
Resources:
• https://csrc.nist.gov/publications/de...
• https://www.ekransystem.com/en/blog/r...
Follow Andrew on Social media:
Twitter: / allthingsiam
Website: Coming soon!!
My other appearances:
CSNP IAM 101: • Identity and Access Management 101
Active Listening: • Sit Down, Shut Up, and Listen – Why A...
Talking IAM with StudioSec: • Andrew Chanthaphone, Founder of All T...
Security Happy Hour with CyberWarrior Studios: • Security Happy Hour: Identity and Acc...
Infosec unplugged with Davin Jackson: • InfoSec Unplugged Talk with Andrew ...
✔ Subscribe for more videos on Identity and Access Management:
/ @allthingsiam
Feel free to leave a comment on suggested topics you want for me to discuss in future videos.
Equipment Used:
Camera: Logitech Brio 4K
Video Editing: Camtasia 2021
Click here for a free trial: https://techsmith.z6rjha.net/P0bnNz
Images and videos provided by Canva
Try it for free: https://bit.ly/3Eaq0B0
Music Epidemic Sound
Try it for free: https://bit.ly/2VM6rxK
Disclaimer: Links included in this description might be affiliate links. If you purchase a product or service with the links, I provide I may receive a small commission. There is no additional charge to you! Thank you for supporting














![Docker Crash Course for Absolute Beginners [NEW]](https://i.ytimg.com/vi/pg19Z8LL06w/mqdefault.jpg)