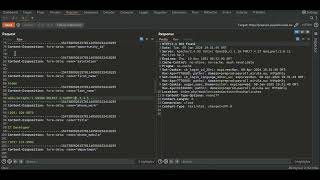
Live Bug Hunting For Beginners: Try to Find the Vulnerability on Live Domain | Bug Bounty | POC 2024
Learn the basics of bug bounty recon and how to find vulnerabilities on a live target. In this video, we'll cover everything you need to know to get started in bug bounty hunting and provide proof of concept for your findings. Get ready to level up your bug hunting game with these essential tips and techniques!
Do you want to learn how to find vulnerabilities on live targets for bug bounty programs? Check out this video for the basics of bug bounty recon and how to successfully find vulnerabilities. Get ahead in the bug bounty game with these tips and become a pro at finding vulnerabilities on live targets for bug bounty programs!
#bugbounty #poc #Delhi #OSINT #Recon #bugbounty #offensivesecurity #redteam #hackerone #hackers #hacking #infosec #hackingtutorial #owasp #educational
Follow me on
Twitter : / officalteambbh
Snapchat: / thebbhx
Telegram : https://t.me/+LCNk1VNEYFYzNWRl
This video is Just for an Educational Purpose.
Welcome to my channel, on my channel I will upload a video about the Bounty bug that I found
I'm just a newbie, N00b Bug Hunter
Help me by clicking the subscribe button and liking :) thanks!
~~~~~~~~~~~Check My latest Video for~~~~~~~~~~~~~~~~~
Path Traversal file deletion in Cisco : • Path Traversal Arbitrary file deletio...
Subdomin Finding: • Finding Subdomain & Make your own Aut...
RCE (Remote Code Execution) Vmware : • RCE (Remote Code Execution) on Vmware...
~~~~~~~~~~~~~~~~~~~~~ ~~~~~~~~~~~~~~~~~~~~~
#oauthmisconfig
#noratelimit
#hackerone
#bugcrowd
#sqli
#xss
#xxe
#bugbounty2022
#sub4sub
#subbot
#bugpoc
#googlebugs
#applebugs
#htmlinjection
#hackeronepoc
#privelagescalation
#businesslogicflaws
#log4j
#99acers
#log4shell
#log4jexploit
#log4j
#log4jrce
#rce
#lfi
#websitepentesting
#idor
#csrf
#ssrf
#bugs2021
#bounty
#teluguhackers
#telugu
#networking
#ffuf
#nuclei
#waybackurls
#nahamsec
#insiderphd
#stokfredik
#pentesting2021
#textinjection
#businesslogicflaws
#infosec
#bughunting
#bughunters
#vikashchowdary
#bughuntingcourse2021
#offensivesecurity
#redteam
#bugbounty |
#hackerone
#hackers
#hackingtutorial
#infosec
#hackingtutorial
#owasp
#educational
#bugpocs
#hackeronelatestpoc
#xsstorce
#xsstolfi
live bug bounty beginners: admin dashboard disclosure
live bug bounty hunting hackerone
live bug bounty
live bug bounty recon
bug bounty account takeover on live website
.:: Hastag #BugBounty ::.
Bug Bounty, bug Bounty PoC, bug Bounty xss, bug Bounty 2021, CVE Exploit ,hackerone, bug Bounty Reward, bug Bounty IDOR, bug Bounty SQL, bug Bounty Account Take Over, bug Bounty rce, bug Bounty write up, parkerzanta, 2fa bypass, XSS on Hidden input, XSS Bug Bounty,HtmlI, Html Injection, critical severity vulnerabilities,owasp vulnerabilities,how to get first bounty,clickup bug bounty,bugbounty,bug bounty,2022 bug pocs hackerone,2022 bug pocs,parameter tampering,buisiness logic flaw,how to get started in bug bouties,xss bug poc,redirect _poc,hackerone bug poc,bugs poc,2022 poc,2022 pocs,reflected xss,cross site .Host Header injection Attack vulnerability,scripting,bugpoc,bugpoc,bug poc,xss poc,bugpocs,hackerone poc,hackerone reports,poc,new pocs 2022,No rate limit,bug bounties,bug bounty for beginners,forgot password,bug bounty poc,noratelimit,public bug bounty disclosure,bug bounty 2020,#bug bounty,open bug sec,#bug hunter,#latest video,#white hat hacker,nordvpn,#cyber security,#indian hackers,#ethical hacking,#dollars,#hacker,hackerone,hackerone bug bounty,hackerone bug bounty beginner,hackerone bug bounty live,bugcrowd,intigriti xss challenge,intigriti bug bounty,intigriti xss,Sql Injection Bypass,
OAUTH MISCONFIGURATION POC,Reflected XSS vulnerability,bug bounty tutorial,
bug bounty methodology,bug bounty for beginners,bug bounty course,bug bounty methodology,bug bounty automation with python, bug bounty automation tools
What Should You Do After Recon?!: Try To Find Vulnerability On Live Target || Bug Bounty || POC 2024
Bug Bounty Secrets: Uncovering Vulnerabilities on Live Targets
Disclaimer:
This video is made available for educational and informational purposes only. We believe that everyone must be aware of ethical hacking and cyber security to avoid different types of cyberattacks on computers, websites, apps, etc. Please regards the word hacking as ethical hacking everytime we use it.
All our videos have been made using our own systems, servers, routers, and websites. It does not contain any illegal activities. Our sole purpose is to raise awareness related to cybersecurity and help our viewers learn ways to defend themselves from any hacking activities. Hacker Vlog is not responsible for any misuse of the provided information










![[Part I] Bug Bounty Hunting for IDORs and Access Control Violations](https://i.ytimg.com/vi/BfbS8uRjeAg/mqdefault.jpg)